Also check out this post about preventive security measures: Microsoft 365 Security / Necessities / Checklist – Prof-IT Services
- Reset account password
- Sign out of all sessions
- Review and remediate Entra ID Protection alerts
- Remove the account from admin roles
- Re-enroll MFA
- Check for enterprise apps authorized for the user
- Scan devices for malware
- Review mailbox rules
- Review mail forwarding
- Move any emails that were deleted/moved to a new folder
- Review audit logs for any other unusual activity
- Unblock the account to allow sending emails
- Enable MFA
- Review email apps and change availability
- Review sign-in logs and check for additional security measures you can take
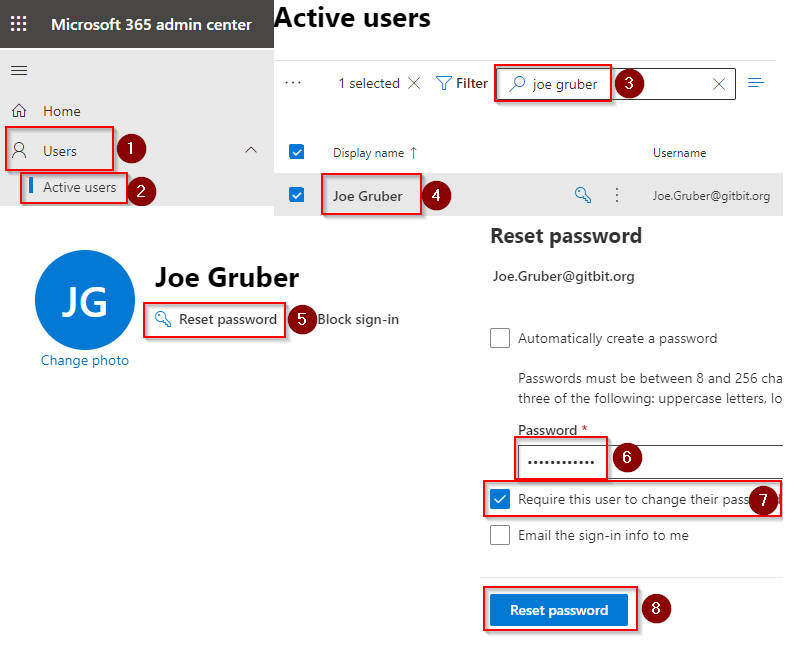
1. Reset account password
First and foremost is locking the hacker out of the account. Reset the password! If it’s a cloud-only account you can reset the user password right from the Microsoft 365 admin center. If it’s a synced account you’ll need to reset the password from your on-premises Active Directory.
- Go to Microsoft 365 admin center > Users > Active Users.
- Search for the user you want to reset the password for.
- Click the Display name of the account.
- Click Reset password.
- Set the password/options as you feel fit and click Reset password.
2. Sign out of all sessions
In short, a session is created every time a user signs into Microsoft 365 on any device/app. What happens is the user will provide the username/password. Microsoft will authorize the connection and then create a session. The device or app will receive an identifying key. Microsoft 365 will hold that key on their end to authorize the app every time the app wants to interact with Microsoft 365. That way the app doesn’t need to send the password every time it is communicating with Microsoft 365. Disconnecting all the user’s sessions will require the user to sign in on all their devices and apps again.
- Go to Microsoft 365 admin center > Users > Active Users.
- Search for the user you want to reset the password for.
- Click the Display name of the account.
- Click Sign out of all sessions.
3. Review and remediate Entra ID Protection alerts
Microsoft Entra ID Protection provides organizations with reporting they can use to investigate identity risks in their environment. These reports include risky users, risky sign-ins, risky workload identities, and risk detections. Investigation of events is key to better understanding and identifying any weak points in your security strategy
Follow this article to resolve open alerts, which could limit the user their functionality.
Investigate risk Microsoft Entra ID Protection – Microsoft Entra ID Protection | Microsoft Learn
Remediate risks and unblock users in Microsoft Entra ID Protection – Microsoft Entra ID Protection | Microsoft Learn
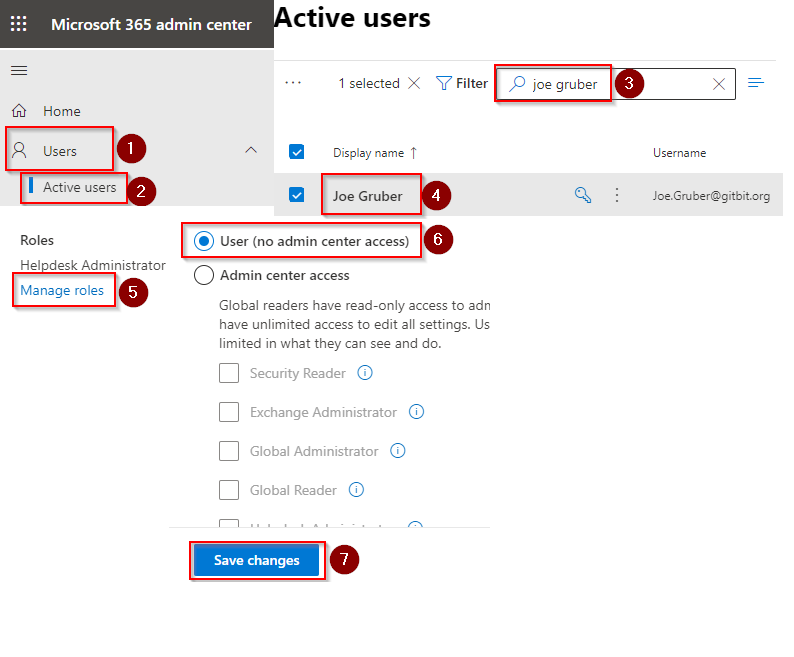
4. Remove the account from admin roles
Next, we may want to remove the account from any admin roles. It’s good practice to temporarily remove the account from any admin roles until you are 100% sure the compromised account is no longer accessed by the hacker.
- Go to Microsoft 365 admin center > Users > Active Users.
- Search for the user you want to reset the password for.
- Click the Display name of the account.
- Click Manage roles > User (no admin center access) > Save changes.
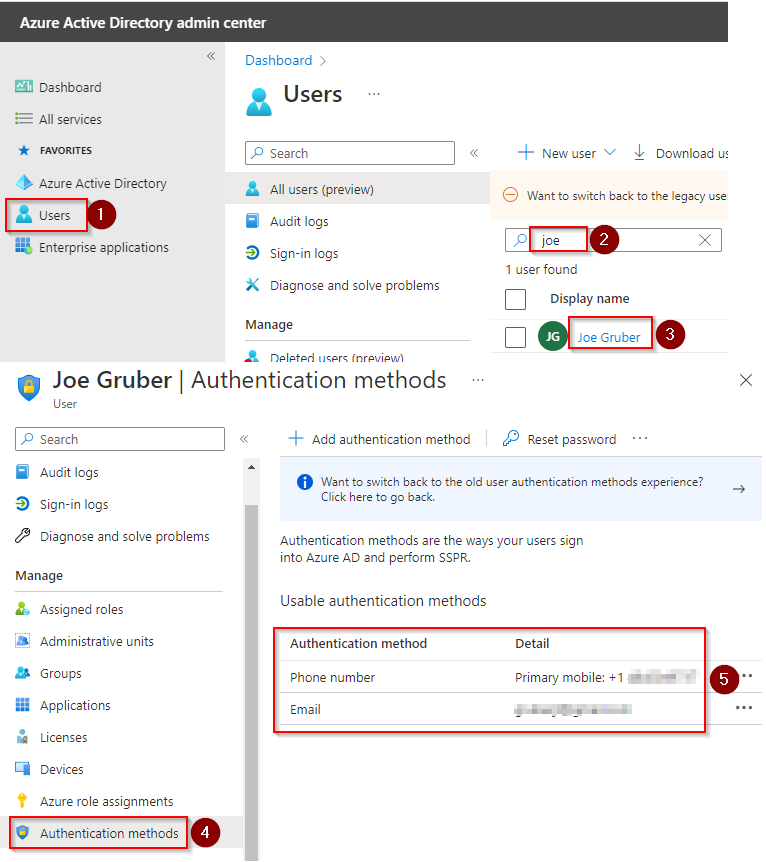
5. Re-enroll in MFA
If you have MFA enabled for the user you may want to re-enroll the devices or at least review the devices and make sure they are the user’s devices. In short, once a malicious user has access to the user’s Microsoft 365 account they can enroll their own devices and possibly reset the password after you’ve changed the password. So go to the user’s MFA authentication methods and sit down with the user and ask if that’s their authentication method.
- Go to Azure Active Directory > Users. Search for the user, then click the user’s display name.
- Click Authentication methods then view the user’s authentication methods.
6. Check for enterprise apps authorized for the user
Another way a malicious actor may retain access to your user’s Microsoft 365 account is through enterprise apps. In short, once a person has access to the account they may register the user for a malicious enterprise app that the hacker can use to retain access to the account after the password reset. So we’ll need to review the registered apps for the user.
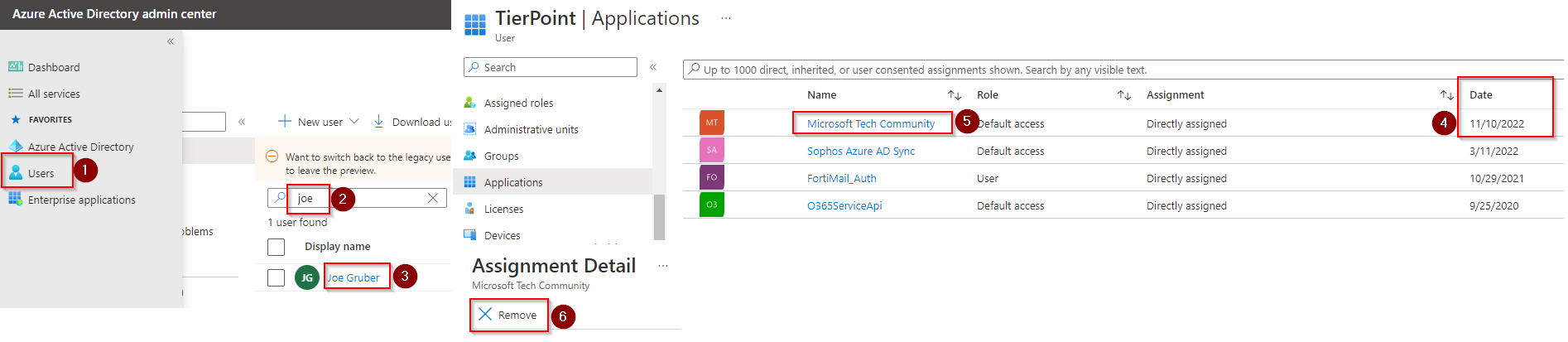
- Go to Azure Active Directory > Users > Search for then click the user’s name.
- Click Applications.
- Sort the list by date.
- Find any apps that were registered since the hacker gained access to the account.
- Click the app name.
- Click Remove.
7. Scan devices for malware
It isn’t very common but I have had an issue where we cleaned the Microsoft 365 account, changed the password, unblocked the account, and then had the malicious actor back in the account! How did they do it? They had malware on the user’s computer. So be sure to scan all the user’s devices for malware. Check for any weird apps in the startup of the computer and check for any strange services.
8. Review mailbox inbox rules
One this hackers like to do once they gain access to one of your mailboxes is send a lot of phishing/spam emails. Of course, sending these emails will return a lot of undeliverable emails and emails from recipients saying things like “Is this legit?”. So One of the ways hackers found to cover their tracks is by creating a mail flow rule that will automatically delete any emails the user receives. There are 2 ways to check for the rules, using the GUI or using PowerShell. Typically, people find the GUI to be more readable so we’ll use that route below. First, you’ll need to grant yourself full access to the mailbox. Then, you’ll need to check for the inbox rules. Finally, you’ll need to remove your full access to the mailbox.
Grant yourself admin rights to the mailbox
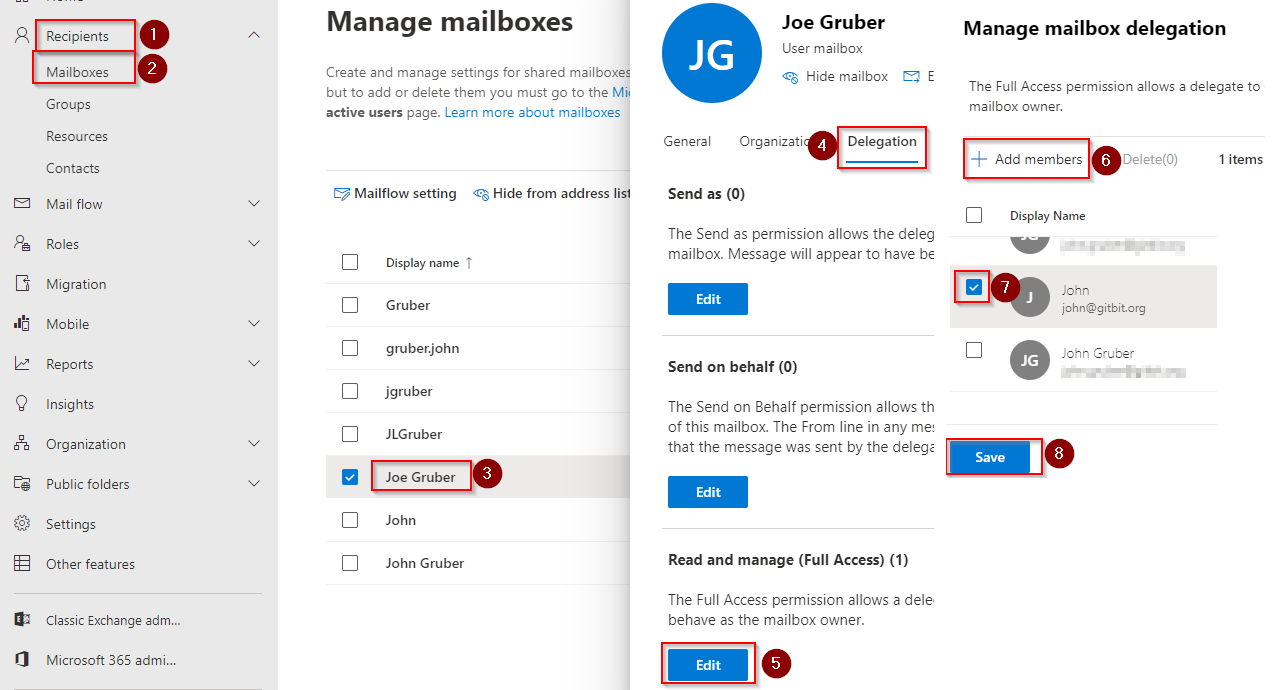
- Open the Exchange admin center > Recipients > Mailboxes.
- Search for and click the Display Name of the user that’s been compromised.
- Click Delegation > Edit (located under Read and manage)
- Click Add members > Click the checkbox next to your admin account. Click Save.
Check the inbox rules
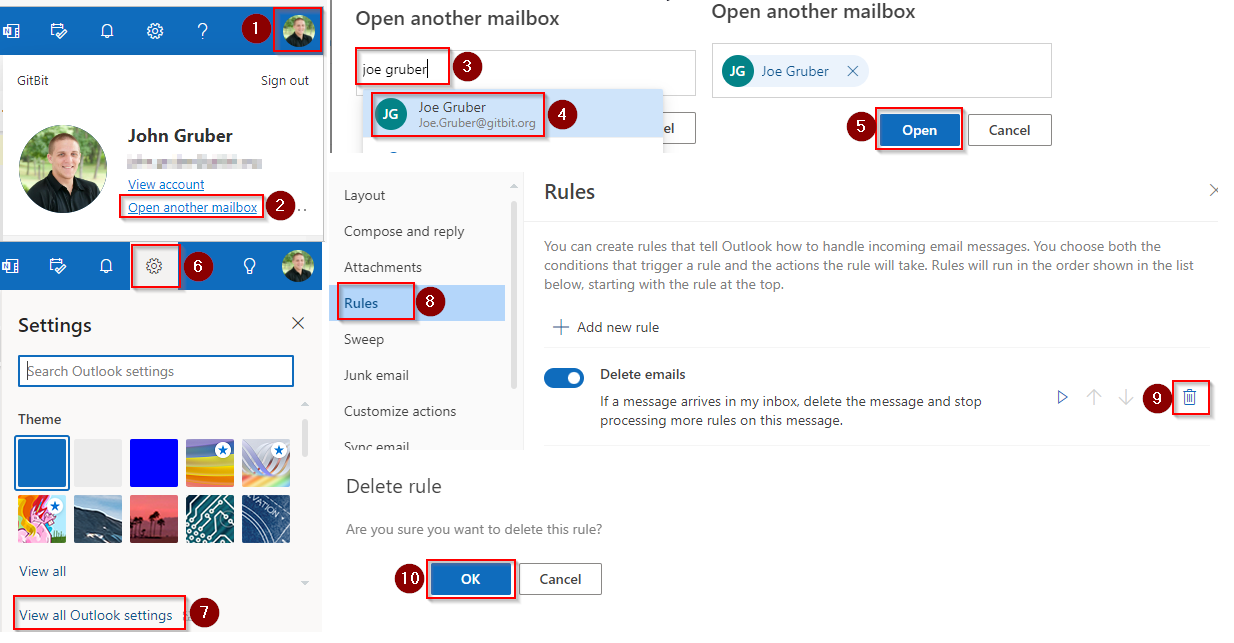
- Open Outlook OWA > Click your profile icon in the top right. Click Open another mailbox.
- Type the user’s display name in the box provided. Click the user that appears in the dropdown. Click Open.
- Click the settings gear in the top right > View all Outlook settings.
- Go to Rules > Click the trash can next to every rule that you want to delete. Click OK.
Before you remove your delegated permissions you should check for mail forwarding. The steps are below.
9. Review mail forwarding
Another thing hackers like to do when they gain access to your mailbox is set up mail forwarding. In short, they may use your account to send phishing attacks to other organizations and request information from other people. So we’ll need to disable any mail forwarding the hacker has set up.

- Open Outlook OWA > Click your profile icon in the top right. Click Open another mailbox.
- Type the user’s display name in the box provided. Click the user that appears in the dropdown. Click Open.
- Click the settings gear in the top right > View all Outlook settings.
- Click Forwarding > uncheck Enable forwarding. Click Save.
Don’t remove those permissions just yet. If you did find an inbox rule or a forwarding rule we’ll need to undo the damage!
10. Move any emails that were deleted/moved to a new folder
In short, you’ll need to move any emails that were deleted or moved to another folder back to the original location. Typically, the original location is the inbox but I’d recommend checking with the user to see if anything else moved or is out of place.
Be sure to go through the email with the user before you move them back.
11. Review audit logs to see if the malicious actor did anything else
Typically, performing everything above is a good measure to undo the damage and access to the malicious user but you never know. Take a quick gander at the audit logs to verify. Especially, if the user account that was compromised was an admin account. The hacker may have dropped in another account and assigned an admin role to it!
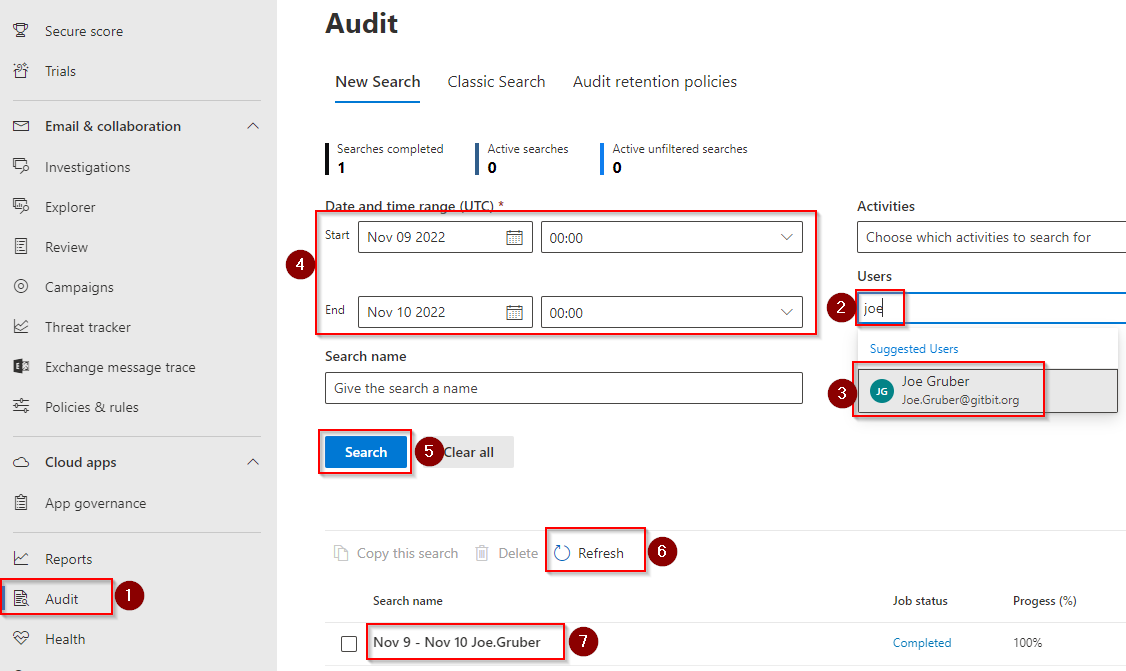
- Go to the Microsoft 365 Defender admin center > Audit.
- Type the user’s name in the Users box. Click the user in the drop-down.
- Enter the start and end times accordingly.
- Click Search. The search will take 5 or more minutes to complete. Click Refresh until the search says “Completed“. Click the search name.
Review the logs or export to CSV for easier filtering and deleting of rows so you can scan through all the content to look for anything else the hacker did.
12. Unblock the account to allow sending emails
Sometimes a malicious actor will get into one of your mailboxes and send a ton of spam. When Microsoft catches a mailbox sending spam they block the mailbox from sending emails. Blocking outbound emails on a mailbox is good for you and the world. It’s good for the world because Microsoft can mitigate hackers from accessing more organizations and spreading their nonsense all over the place. It’s good for you and your organization because it prevents damage to your company’s reputation. Anyway, let’s jump in and unblock the account.
- Go to Microsoft 365 Defender admin center > Review > Restricted entities.
- Click the user in the list. Click Unblock > Next > Submit > Yes.
13. Enable MFA
If MFA isn’t already enabled I would recommend it. It’s a great second line of defense in case a user has their password stolen. There are several ways to enable MFA in a tenant / for a user in Microsoft 365. That’s already covered in The many ways to implement multi-factor authentication (MFA) in Microsoft 365. So I won’t go into detail about it. But you really should consider enabling MFA.
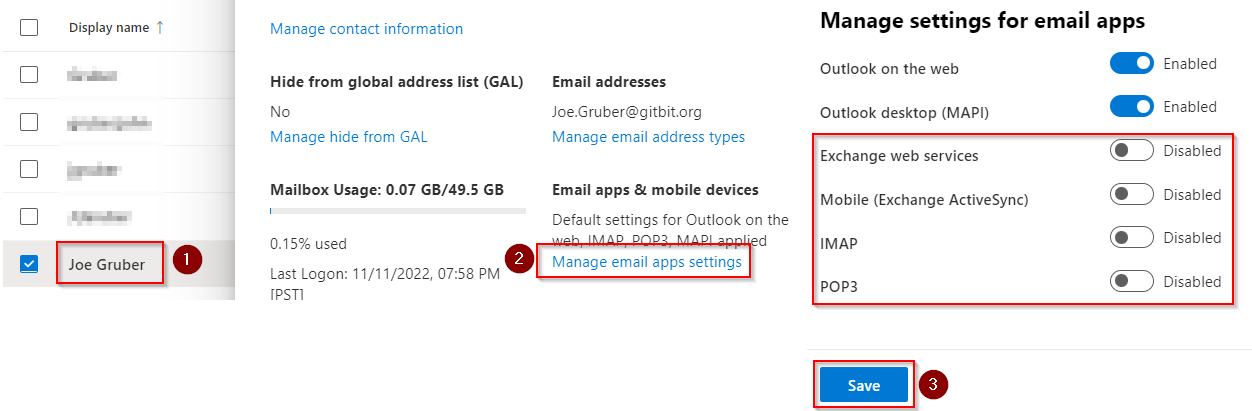
14. Review email apps and change availability
Next up on the list of hardening your environment, is disabling unused email apps. What happens a lot of times is the hacker will gain entry into the user’s mailbox and then set up an IMAP or a POP connection to the mailbox to send out the spam/phishing emails to everyone else. Assuming your users are using the browser or a modern application, for example, Outlook then we can go ahead and disable those email apps. You can disable the email apps using a conditional access policy but I didn’t want to write a book so I’m going to show you how to disable it for a user. I’ll write another article on conditional access policies that will have that listed so stay tuned!

- Open Exchange admin center > Recipients > Mailboxes.
- Search for, then click on the user you want to disable the email apps.
- Click the toggle switch to Disabled for any email apps the user isn’t using. Click Save.
15. Review sign-in logs and check for additional security measures you can take
Finally, we have almost finished with the compromised account. The last step is looking into how the hacker breached the account and then hardening that part of Microsoft 365. Did the hacker log in from Russia? Do you do business / have users logging in from Russia? No, then create a conditional access policy limiting sign-ins from Russia. Or maybe the user account was breached because the user received a phishing email and then clicked a link and entered their credentials in a fake Microsoft 365 sign-in portal. Then set up Safe Links. To review the sign-in logs perform the following:
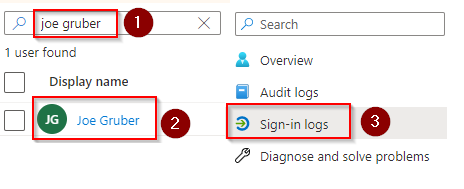
- Go to Microsoft Azure Active Directory admin Center > Users.
- Search for the user that was breached and click on his/her display name.
- Click Sign in Logs.
Credit to 14 steps to fix a hacked Microsoft 365 account – GitBit (we added an additional step).

No responses yet